In-Depth Look at Chainalysis, Elliptic, and CipherTrace: Forensic Science in Blockchain Analysis | The Truth About Forensic Science

Elliptic Curve Based Cybersecurity Schemes for MQTT in IoT - Contiki Cooja Project | S-Logix | S-Logix

Sensors | Free Full-Text | Elliptic Curve Cryptography Considerations for Securing Automation and SCADA Systems

Waikato students take out the grand prize for the NZ Cyber Security Challenge - News and Opinion: University of Waikato

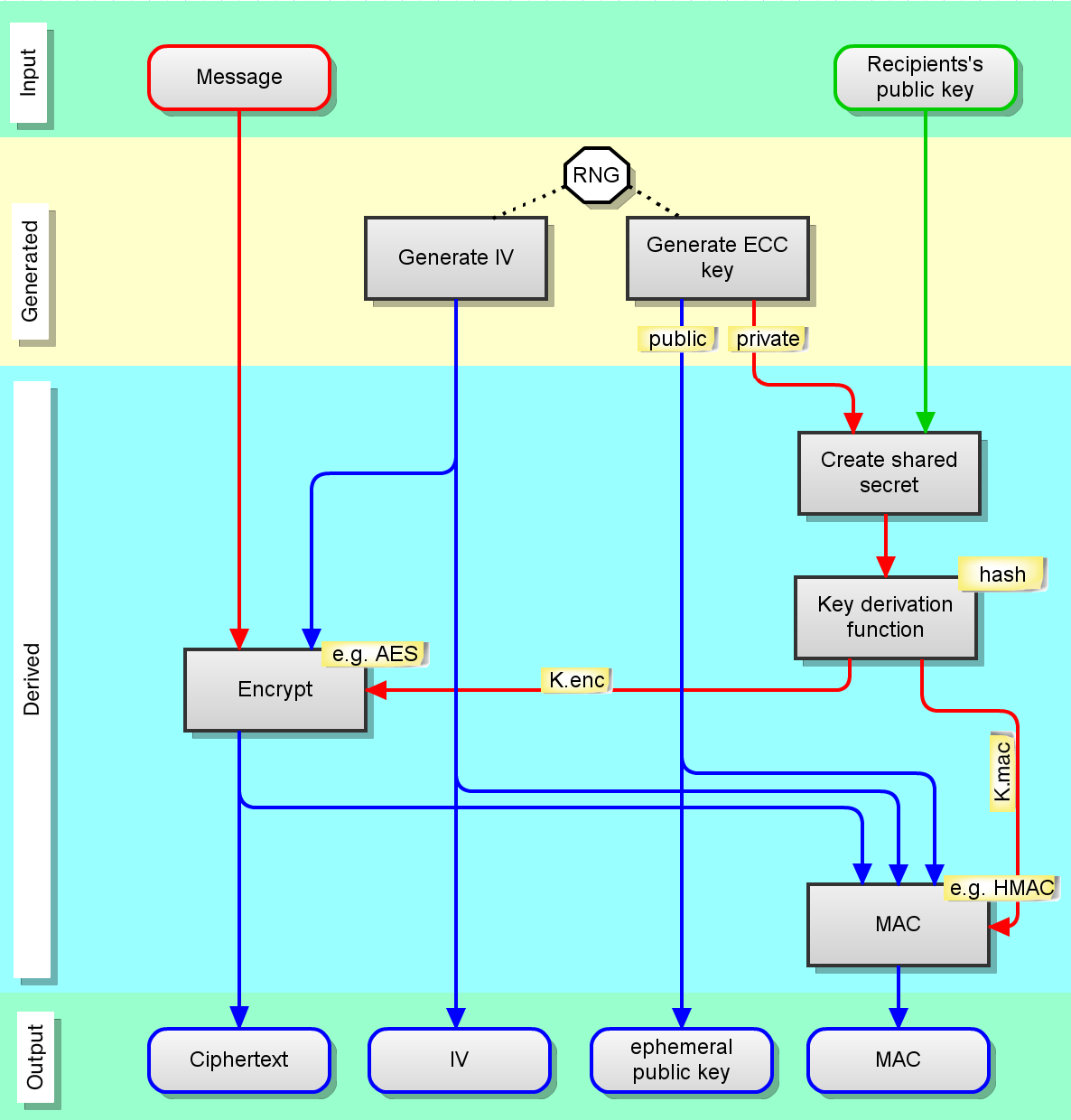
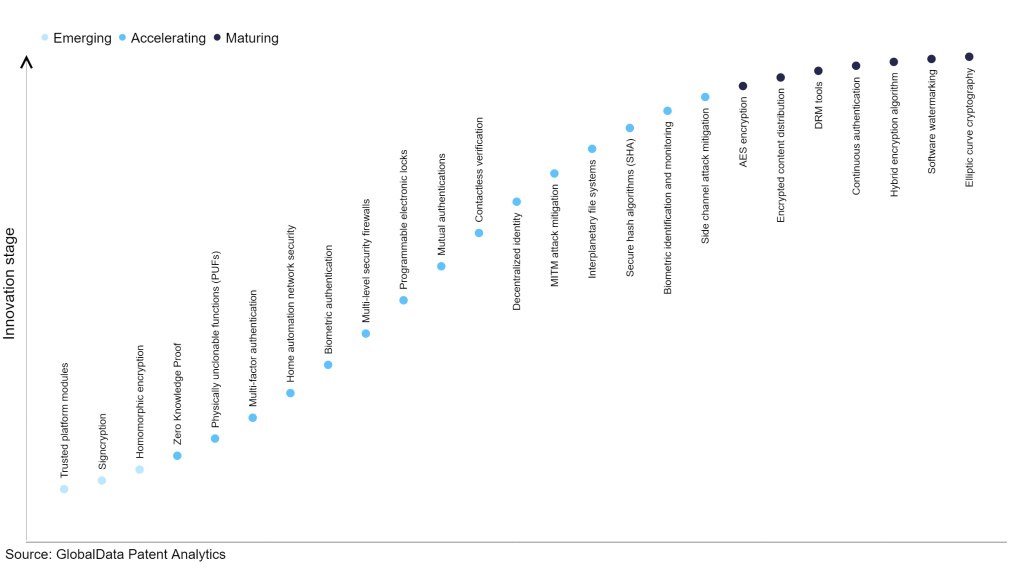
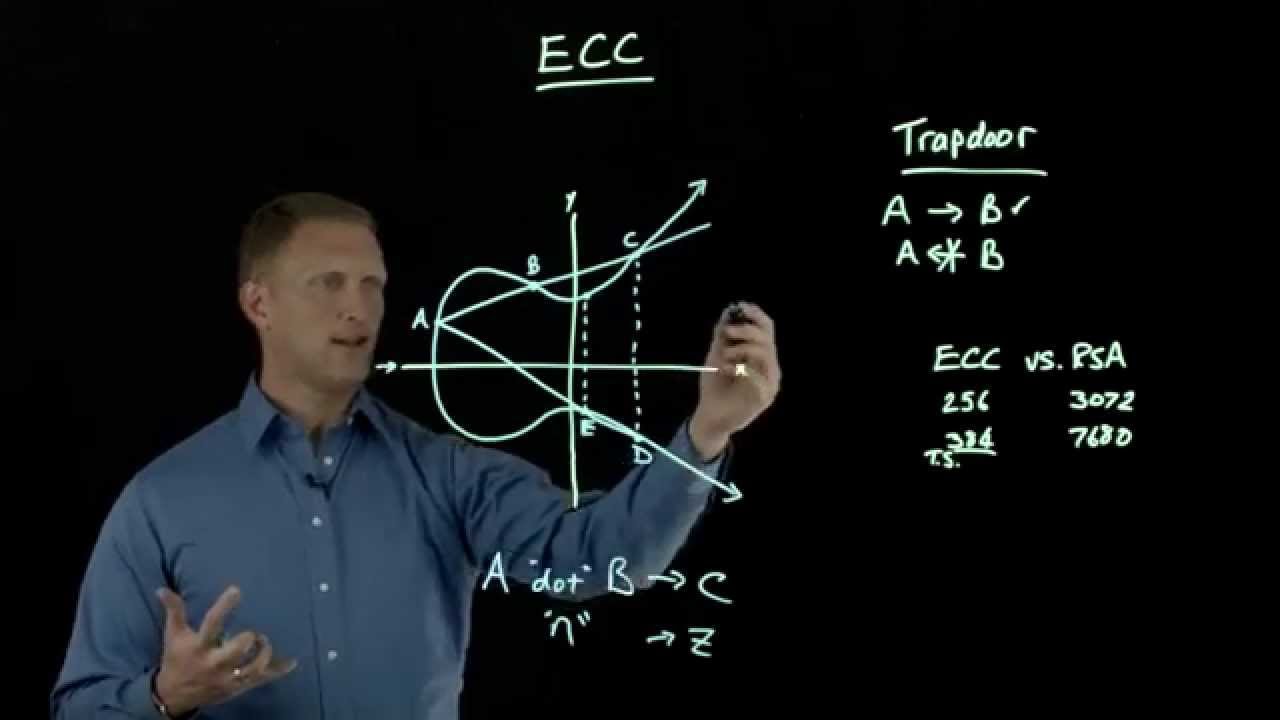
ECC Algorithm to Enhance Security with Better Key Strength | Algorithm, Security, Cryptography algorithms